Authors:
(1) Amit Seal Ami, Computer Science Department, William & Mary Williamsburg, Virginia, USA, and this author contributed equally to this paper (aami@wm.edu);
(2) Syed Yusuf Ahmed, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper (bsse1013@iit.du.ac.bd);
(3) Radowan Mahmud Redoy, Institute for Information Technology, University of Dhaka Dhaka, Bangladesh, and this author contributed equally to this paper (bsse1002@iit.du.ac.bd);
(4) Nathan Cooper, Computer Science Department, William & Mary Williamsburg, Virginia, USA (nacooper01@wm.edu);
(5) Kaushal Kafle, Computer Science Department, William & Mary Williamsburg, Virginia, USA (kkafle@wm.edu);
(6) Kevin Moran, Department of Computer Science, University of Central Florida Orlando, Florida, USA (kpmoran@ucf.edu);
(7) Denys Poshyvanyk, Computer Science Department, William & Mary Williamsburg, Virginia, USA (denys@cs.wm.edu);
(8) Adwait Nadkarni, Computer Science Department, William & Mary Williamsburg, Virginia, USA (apnadkarni@wm.edu).
Table of Links
6 Future Work and Conclusion, Acknowledgments, and References
4 IMPLEMENTATION OF MASC
To satisfy the design goals (DG1–DG4), we implemented MASC (11𝐾+ effective Java source line of code) following single-responsibility principle across modules, classes, and functions. Note that while current implementation of MASC inherits the mutation scopes of the original implementation with internal structural changes, the bulk of the changes with new features in the current implementation of MASC are based on the Main Scope. Therefore, we describe the implementation details of MASC with a focus on Main Scope in the context of the design goals and provide an overview of the architecture in Figure 2.
Configuration Manager: To make MASC as flexible as possible, we decoupled the crypto-API specific parameters from the internal structure of MASC. As a result, user can specify any crypto-API along with its necessary parameters through an external configuration file defining the base crypto-API misuse case. The configuration file follows a key-value format, as shown in Listing 2. Additionally, user can specify the mutation operators and scope to be used, along with other configuration values, thus satisfying DG1.
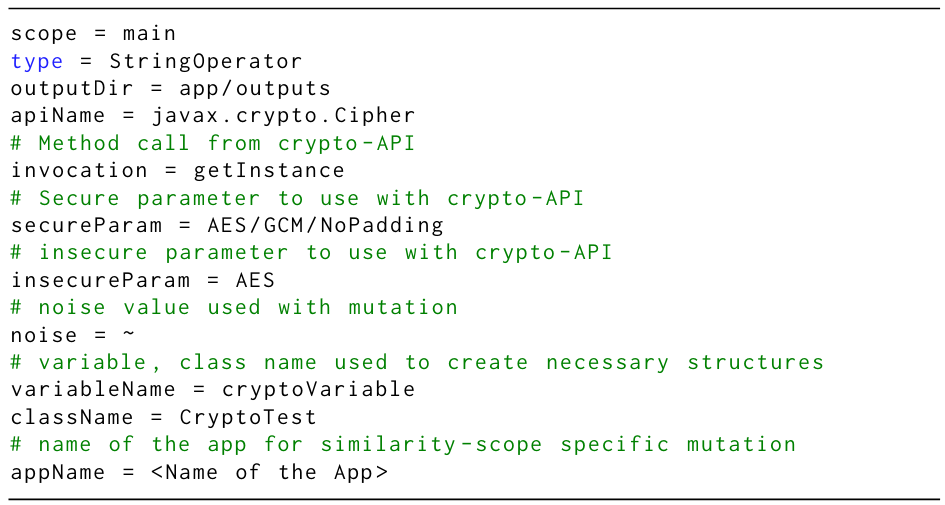
Mutation Operator Module: MASC analyzes the specified cryptoAPI and uses the values specified by the user (e.g., secure, and insecure parameters to be used with the API) for creating mutated crypto-API misuse instances. Internally, the decoupling of cryptoAPIs from MASC is made possible through the use of Java Reflection based API analysis and Java Source Generation using the Java Poetry Library (DG1). While both the original and current implementation of MASC comes with several generalizable mutation operators, the current implementation of MASC includes an additional plug-in structure that facilitates creating custom mutation operators and custom key-value pairs for the configuration file. Both of these can be done externally, i.e., no modification to source code of MASC is necessary (DG2). We provide additional details about MASC’s mutation operators in Section 4.1.
Automated Evaluation Module: The current implementation of MASC leverages the SARIF formatted output to automate evaluation of crypto-detectors. To make end-to-end analysis automated, MASC’s can be configured to use crypto-detector specific commands, such as e.g., compiling a mutated source code for analysis, evaluation stop conditions, command for running crypto-detector, output directory, and more (DG3–DG4).
Furthermore, MASC is implemented to produce verbose logs. With the combination of flexible configuration, it is therefore possible to use the stand-alone binary MASC jar file as a module of another software. As a proof of concept, we implemented MASC Web, a python-django based front-end that offers all the functionalities of the MASC (Usage details in Section 5) that uses the binary jar of MASC as a module (DG4).
This paper is available on arxiv under CC BY-NC-SA 4.0 DEED license.